Threat from Virtual to Reality: Let's talk about the safety of autonomous driving
Lei Feng network press: This article is Lei Feng network exclusive first article, the author song, co-founder and CTO of Seattle Newsky Security company, the industry's well-known anti-virus experts, hackers, Lei Feng Wang column contributing author.

The driver’s death was caused by the automatic driving accident of Tesla this time. It has been nearly two months since the incident, but it has been a matter of several days in the media. According to official analysis, the reason for the incident was that the autopilot sensor misjudged a large truck with a high chassis and misjudged it as a bridge and other buildings. We can see that computer errors are no longer confined to the virtual world, but can lead to the loss of human life. As a computer security researcher, we must not only ask what may happen to the on-board computer, but also lead to serious accidents .
Let's start with OBD II, the on-board diagnostic system in the United States . OBD II is the meaning of On-Board Diagnostics Version II. It happened to be the 20th anniversary of the implementation of OBD II in the United States this year. The U.S. stipulates that beginning in 1996, cars sold in the United States must have an OBD II system. The OBD II is the interface to the car controller network, typically in front of the driver's left knee.
For example, the OBD II interface of Tesla Model S is:

(Figure 1: OBD II interface of Tesla Model S)
Most cars run by the United States, whether made in the United States, Japan, or Europe, use such interfaces.
Connect this interface, you can connect to the car controller bus CAN Bus, and then chat with the various computer inside the car, such as let the engine controller tell you that today drank a few pots, ah, ask if the oil is too hot , tell the brake ABS controller to let go ah and the like.
The problem has come. When the OBD II standard was established, there was no wireless interface on the car . It should be pointed out that wired networks and wireless networks are completely different security games. Because of the signal connection of the wired network, an implicit trust architecture was constructed through the cable. Only trusted computers can connect to the network. This is like a group of children who have grown up in key schools. Everyone is ethical, polite, and completely unaware of the sinister nature of the outside world.
The wireless network is a jungle. Everyone can eavesdrop, anyone can speak, and everyone can imitate others. To connect a device on a wired network to a wireless network is equivalent to throwing a group of embarrassing children directly into the food market. It is certain that a few are defrauded. Do not believe? You may wish to listen to the 2.4G Hz frequency band, where there are Bluetooth, BLE and Zigbee shallow, WiFi sings, wireless mouse squatting, remote control toy noise, there is a broken cordless phone, suddenly everyone It was all quiet, and only the roar of the microwave oven was in my ears.
The computers in the car, after 20 years, found that the various devices around them could all pass through the wireless interface. Whether it was a car phone, car WiFi, or Bluetooth, it was connected to the CAN bus and told that the engine controller should rest, or ABS controller should let go. And hackers can also use these wireless interfaces to chat with a controller on a moving car and think about it.
We still have a measure of this type of attack that may have serious consequences. Here is a less serious example.
In the previous period of domestic innovation boom, many people had car networking. The so-called car networking, many programs is actually to buy this small box into the car's OBD II interface, and then use the phone and a small box inside the Bluetooth pairing, the phone's APP can read the CAN bus through the OBD II interface above A variety of information, including oxygen consumption, engine speed, and more.

OBD II plug
The problem is that neither this small box nor the CAN bus has enough precautions to stop hackers from attacking. The first attack we made was to drive a car on the road and use a mobile phone to scan the wireless signal of this small box. Once discovered, the pairing is deciphered (in the "Suspect Tracking", the upper body of the house is forbidden). Then you can read some of the car's sensitive information. In fact, we do not take any other sensitive information, is to find the VIN of the ECU to ask the car (equivalent to the car's ID card) ah, ask the car is not hot like ah. These can be asked from the side of the car within half a minute of the red light. Another time in the driving process is to let the next car tell us what its speed is.
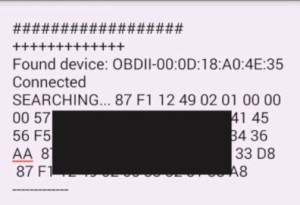
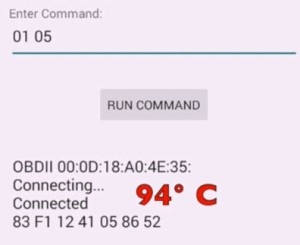
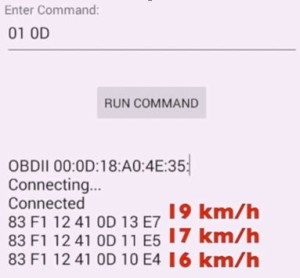
Tesla is doing very well in isolating the OBD II from the on-board controllers. Tesla's OBD II interface simply provides voltage and ground as required by law, but it does not have data connectivity to the on-board controller. In contrast, Tesla's control computer has wifi and Ethernet interfaces. These interfaces can also be used as hacking interfaces.
We talked about the methods that traditional vehicle controllers can be attacked by hackers. In terms of autonomous driving, the car has added new sensors and computers that traditional cars do not have. For example, a computer vision camera is used to detect objects in and around a lane; for example, GPS that was not connected to a driving controller is now connected as a data input to the driving control network; there are also lidars. All these new sensors will continuously input data to the control computer. When the input data is disturbed, it may disturb the normal operation of the computer in the driving control network and cause an accident.

The third type of third-party program that causes the fault of the on-board system. Everyone may still remember that Jobs still did not want the App Store when the iPhone was released. The reason is actually very simple. In an open computer system, about three-quarters or more of the system crashes come from third-party programs. When I was reading a book, a professor once showed us a paper. According to statistics, third-party drivers in Microsoft's Windows system caused about 80% of system crashes. Jobs's threat to third-party programs is also very clear. Many in-vehicle systems now require third-party programs for entertainment, such as playing network music, displaying destination weather, etc. These third-party programs are often not guaranteed to be as secure as the rest of the system.
As a specially invited security expert of the W3C Workplace Networking Team of the International Organization for Standardization of the Internet, I also made some suggestions on the security of third-party programs in the meetings of the IoV Working Group and received great attention. Those who are involved in the establishment of standards have attached great importance to the safety of onboard systems. We will have a special safety conference to discuss the safety of onboard systems.
Lei Feng network (search "Lei Feng network" public concern) Note: Reprinted, please contact Lei Feng network authorization, and retain the source and author, not to delete the content.
Toy Sound Module, Musical Module for Toys, Waterproof Sound Module
AST Industry Co.,LTD , https://www.astsoundchip.com